Evolving Microsoft SmartScreen to protect you from drive-by attacks
Today, we’re happy to announce that with the latest Windows 10 updates, we’ve extended SmartScreen to include protection from drive-by attacks in Microsoft Edge and Internet Explorer 11.
What is a drive-by attack?
Drive-by attacks are malicious web attacks that tend to start on trusted websites, targeting security vulnerabilities in commonly used software. What’s more, they often don’t require any user interaction – so there’s nothing to click, nothing to download – and infection is usually invisible.
Drive-by attacks make use of services known as exploit kits (EKs) to scale effectively. These are tools that first check your PC for software vulnerabilities (tracked publicly as CVEs) and then try to exploit them. The vulnerabilities can be either newly discovered ones – also known as 0-days – or ones that have already been fixed in popular software. Over the past year, we’ve seen EKs moving faster to target vulnerabilities in apps with available patches, while also exploiting 0-day vulnerabilities more frequently as well.
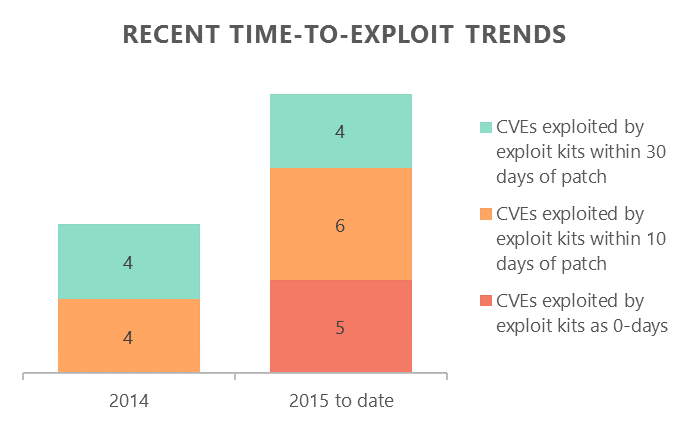
Given this trend, users have less time to update to a secure state and can no longer rely on staying patched as a reliable EK defense. Fortunately, Microsoft has cultivated a broad set of data from sources like Microsoft Edge, Internet Explorer, Bing, Defender and the Enhanced Mitigation Experience Toolkit (EMET) to be able to see these attacks as they emerge, and to turn this information into the intelligence that powers SmartScreen drive-by protection in the browser.
This cross-company data intelligence effort is unique since it brings together information not just about the browsing experience or web infrastructure, but also about behavioral telemetry from across the Windows operating system. This can help us to detect potential attacks in progress and detect emerging threats.
To illustrate how this works, let’s look at a specific case study. Last December, as part of the development of this new SmartScreen capability, multiple Microsoft data sources including Defender and EMET picked up a new set of exploit attacks targeting millions of users through a network of malicious ads displayed on popular sites. The threat, broadly referred to as the HanJuan EK, was detected by SmartScreen’s exploit intelligence systems. As we dug into the data, we discovered the attack was actually leveraging a new 0-day exploit in Adobe Flash player, meaning that SmartScreen intelligence systems were detecting this attack even before it was identified as a new 0-day exploit. We reported the issue privately to Adobe (CVE-2015-0313) and a patch was developed and shipped.
With SmartScreen drive-by protection, these types of threats may be prevented before a user is infected, even if a patch isn’t yet available.
How has SmartScreen evolved to help me?
Unlike existing SmartScreen protection from socially engineered attacks, drive-by attacks need to be detected and prevented before any web content is parsed and rendered. To avoid impacting browsing performance, SmartScreen helps protect against drive-by attacks by using a small cache file created by the SmartScreen service. This cache file is periodically updated by your browser to help keep you protected and to ensure that calls to the SmartScreen service are only made if we believe there’s a high probability of malicious content on a page.
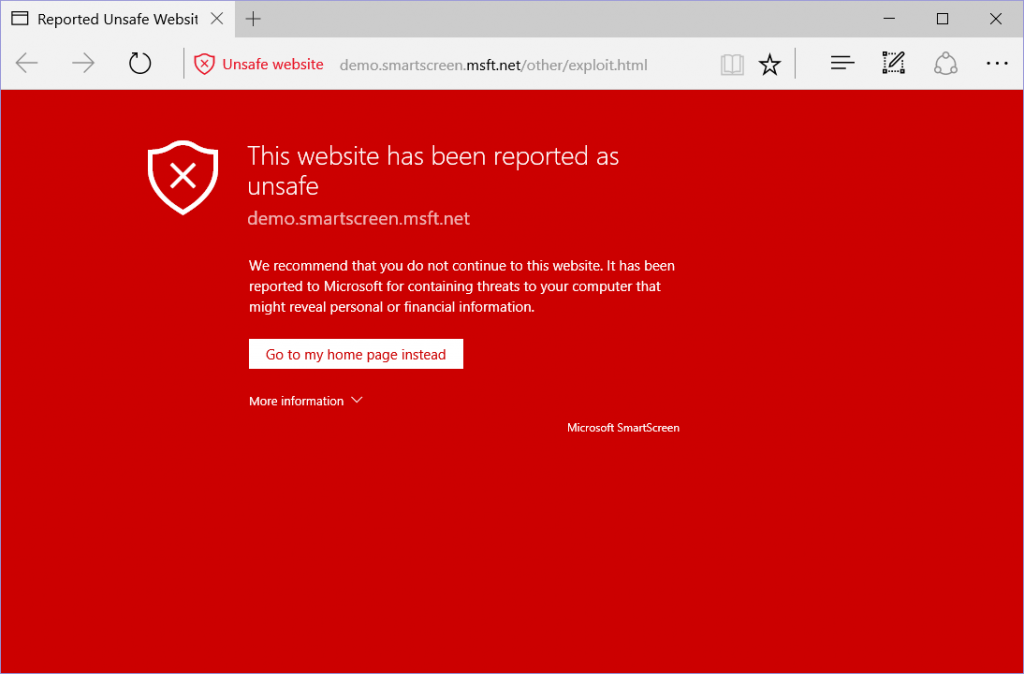
If SmartScreen determines that a website is potentially malicious, you’ll see a red warning and the content won’t render in either Microsoft Edge or Internet Explorer 11 on Windows 10.
SmartScreen also has the ability to warn you about potentially malicious frames, such as unsafe ads. In the past, unsafe frames on a page would result in a full-page warning, even if the webpage hosting the content was safe. Now, SmartScreen can show you warnings for only the frames that are found to be malicious, letting you continue to interact with the rest of the page.
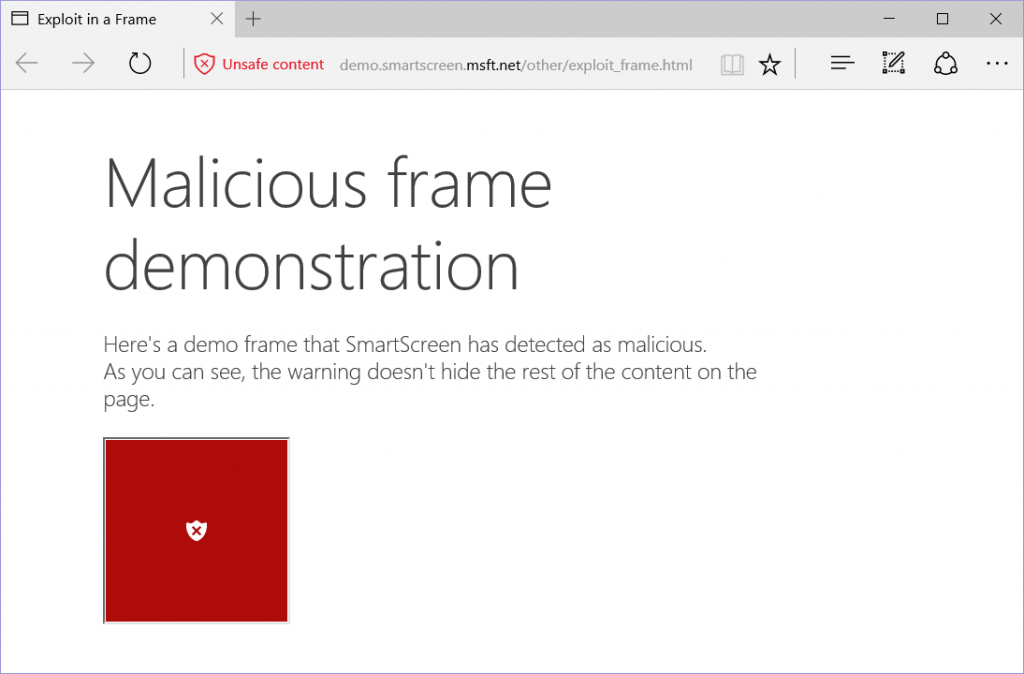
You can expand the More Information link on the SmartScreen warning page to report a site as safe to Microsoft or to bypass the warning – though we highly recommend that you don’t bypass it. For warnings shown in frames, you can click the Unsafe Content badge in the address bar for the same options
Note: All existing SmartScreen settings and controls (including Group Policy) apply to SmartScreen’s new drive-by attack protection.
Is there anything else I can do?
When drive-by attacks target vulnerabilities that have already been fixed in popular software, your browser, or your operating system, it’s vital that you install security updates when they become available.
Additionally, if you find a site that you think is unsafe, you can report it to Microsoft using:
- Microsoft Edge on Windows 10. Tap or click the More menu, choose Send feedback, and then choose Report unsafe website.
- Internet Explorer 11 on Windows 10. Tap or click the Tools button
 , point to Safety, and then choose Report unsafe website.
, point to Safety, and then choose Report unsafe website.
We’re excited about these improvements and look forward to hearing your feedback! If you have any questions, please don’t hesitate to reach out to us @MSEdgeDev on Twitter or in the comments below.
– Jasika Bawa, Program Manager, OS Security
– Ryan Colvin, Senior Program Manager, SmartScreen
