Introducing Windows Defender Application Guard for Microsoft Edge
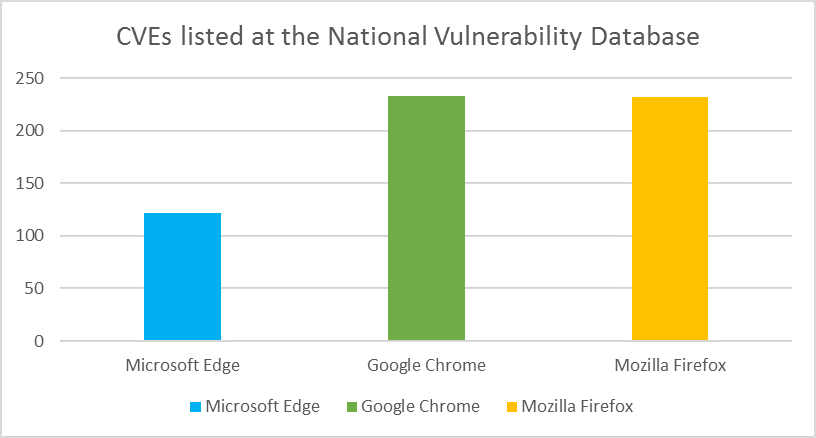
While no modern browser—or any complex application—is free of vulnerabilities, the majority of the vulnerabilities for Microsoft Edge have been responsibly reported by professional security researchers who work with the Microsoft Security Response Center (MSRC) and the Microsoft Edge team to ensure customers are protected well before any attacker might use these vulnerabilities in the wild. Even better, there is no evidence that any vulnerabilities have been exploited in the wild as zero-day attacks.
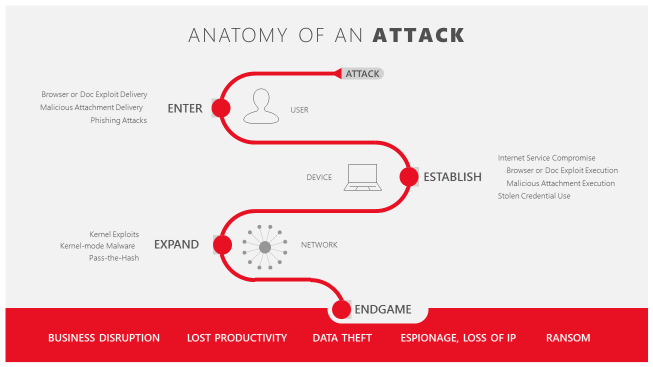
However, many businesses worldwide have come under increasing threat of targeted attacks, where attackers are crafting specialized attacks against a particular business, attempting to take control of corporate networks and data. For the most security-conscience businesses, we are introducing a new layer of defense-in-depth protection: Windows Defender Application Guard for Windows 10 Enterprise. Application Guard provides unprecedented protection against targeted threats using Microsoft’s Hyper-V virtualization technology.
Understanding targeted attacks against large Enterprises
The threat landscape has changed significantly in recent years. Today, over 90% of attacks use a hyperlink to initiate the attack to steal credentials, install malware, or exploit vulnerabilities.
This is damaging not only to the business attacked, but also to the thousands, if not millions of users whose accounts and personal data may be stolen. Highly motivated and persistent attackers will often start with a social engineering trick: creating a well-crafted and personal email to known employees of the company. This email, which will often appear to be from a legitimate authority in the company, may ask the employee to click a link to read a supposedly important document. Unfortunately, that link is to a specially crafted malicious web site that may use a previously undisclosed vulnerability to install malware on the user’s machine. Once established on that single computer, the attackers can then steal credentials and start to probe the rest of the network for other vulnerable machines, repeating the process on other computers until they achieve their objective, whether that is stealing data, intellectual property, or disrupting the business.
Breaking the attacker playbook
We’re taking a systematic approach to disrupting these attackers by providing our customers with the tools they need to defend against these vectors of attack. Application Guard is designed to stop attackers from establishing a foothold on the local machine or from expanding out into the rest of the corporate network.
By using our industry leading virtualization technology, potential threats are not only isolated from the network and system, but will be completely removed when the container is closed.
Digging deeper into Application Guard
Application Guard leverages virtualization technology born in the Microsoft Cloud to accomplish this disruption.
When a user browses to a trusted web site, for example an internal accounting system web application, Microsoft Edge operates as it does today. It has access to local storage, can authenticate the user to internal sites with corporate credentials, standard cookies work, the user can save files to the local machine, and in general Windows just works. This mode, outlined in blue in the chart below, is known as the Host version of Windows.
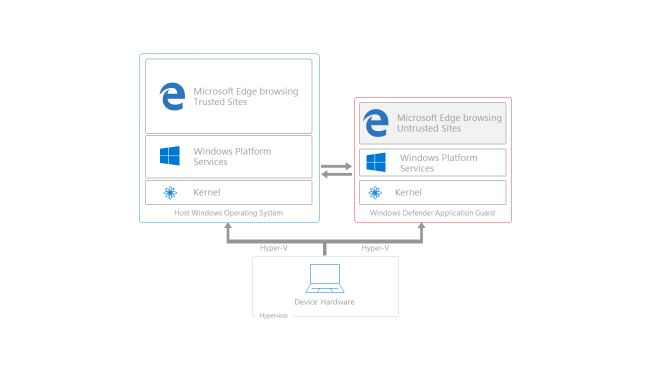
However, when an employee browses to a site that is not recognized or trusted by the network administrator, Application Guard steps in to isolate the potential threat. As shown in the mode outlined in red above, Application Guard creates a new instance of Windows at the hardware layer, with an entirely separate copy of the kernel and the minimum Windows Platform Services required to run Microsoft Edge. The underlying hardware enforces that this separate copy of Windows has no access to the user’s normal operating environment.
Application Guard’s enforcement includes completely blocking access to memory, local storage, other installed applications, corporate network endpoints, or any other resources of interest to the attacker. This separate copy of Windows has no access to any credentials, including domain credentials, that may be stored in the permanent credential store.
Most of the time, even untrusted sites are not malicious and perfectly safe to visit, and the user just expects them to work. This isolated environment allows these sites to function essentially as they would if they were running on the host version of Windows. In this case Application Guard does provide the essential features that users would expect to work, even when browsing untrusted sites, such as being able to copy and paste with the Windows clipboard, and being able to print content from those web sites to their work printer. This allows the user to still be productive even while the host is being protected by Application Guard. The enterprise administrator has control over this functionality using Microsoft management tools and policy, and can choose what they are comfortable with based on their own risk assessment.
Defense-in-depth isolation for enterprises
To improve on the security offered by purely software based sandboxes, Microsoft worked with several enterprise and government customers on a hardware based isolation approach to address these concerns. With Application Guard, Microsoft Edge protects your enterprise from advanced attacks that can infiltrate your network and devices via the Internet, creating a safer, worry-free browsing experience for customers.
But what happens when the untrusted site is actually part of an attacker’s malicious plan? Let’s revisit the attack described above. An attacker sends a well-crafted email to an innocent employee of the company enticing them to visit a link on a site under the attacker’s control. The innocent user, not noticing anything suspicious about the mail, clicks on the link to an untrusted location. In order to proactively keep the user and enterprise resources safe, Application Guard coordinates with Microsoft Edge to open that site in a temporary and isolated copy of Windows. In this case, even if the attacker’s code is successful in attempting to exploit the browser, the attacker finds their code running in a clean environment with no interesting data, no access to any user credentials, and no access to other endpoints on the corporate network. The attack is completely disrupted. As soon as the user is done, whether or not they are even aware of the attack having taken place, this temporary container is thrown away, and any malware is discarded along with it. There is no way for the attacker to persist on that local machine, and even a compromised browser instance has no foothold to mount further attacks against the company’s network. After deletion, a fresh new container is created for future browsing sessions.
Web developers and Application Guard
The good news for web developers is that they do not need to do anything different with their site code – Microsoft Edge renders sites in Application Guard fundamentally the same way it does in the host version of Windows. There is no need to detect when Microsoft Edge is running in this mode, nor any need to account for behavior differences. Since this temporary container is destroyed when the user is done, there is no persistence of any cookies or local storage when the user is finished.
We’re committed to keeping Enterprise users and data safe and secure
Our mission at Microsoft is to empower every person and every organization on the planet to achieve more. With Windows Defender Application Guard, enterprise users can take advantage of the vast power of Internet sites and services while still protecting corporate and personal data. This capability makes Microsoft Edge the most secure browser for the Enterprise.
Windows Defender Application Guard for Microsoft Edge will become available to Windows Insiders in the coming months, and roll out more broadly next year.
― John Hazen, Principal Program Manager, Microsoft Edge
― Chas Jeffries, Principal Program Manager, Application Guard