Today we are pleased to release the first build of the Windows Server 2019 Long-Term Servicing Channel (LTSC) release that contains both the Desktop Experience as well as Server Core in all 18 server languages, as well as the first build of the next Windows Server Semi-Annual Channel release.
What’s New in Windows Server 2019 Insider Preview Build 17623
For every preview release, we will provide a focus area that we would like you to take a look at and provide us with feedback on. We encourage you to try out any functionality in the release and we welcome your feedback.
Validation for every preview: There are two major areas that we would like you to try out in each preview release and report back any issues:
- In-place OS Upgrade (from Windows Server 2012 R2, Windows Server 2016)
- Application compatibility – please let us know if any server roles or applications stops working or fails to function as it used to
Extending your Clusters with Cluster Sets
“Cluster Sets” is the new cloud scale-out technology in this Preview release that increases cluster node count in a single SDDC (Software-Defined Data Center) cloud by orders of magnitude. A Cluster Set is a loosely-coupled grouping of multiple Failover Clusters: compute, storage or hyper-converged. Cluster Sets technology enables virtual machine fluidity across member clusters within a Cluster Set and a unified storage namespace across the “set” in support of virtual machine fluidity. While preserving existing Failover Cluster management experiences on member clusters, a Cluster Set instance additionally offers key use cases around lifecycle management of a Cluster Set at the aggregate.
Windows Defender Advanced Threat Protection
Available in this preview, we provide deep platform sensors and response actions, providing visibility to memory and kernel level attacker activities and abilities to take actions on compromised machines in response to incidents such as remote collection of additional forensic data, remediating malicious files, terminating malicious processes etc.
If you’re already using Windows Defender ATP – preview these features by simply installing the latest Windows Server preview build and onboard it to Windows Defender ATP.
Otherwise – sign up to Windows Defender ATP trial here
Windows Defender ATP Exploit Guard
Windows Defender ATP Exploit Guard is a new set of host intrusion prevention capabilities. The four components of Windows Defender Exploit Guard are designed to lock down the device against a wide variety of attack vectors and block behaviors commonly used in malware attacks, while enabling enterprises to balance their security risk and productivity requirements.
- Attack Surface Reduction (ASR): A set of controls that enterprises can enable to prevent malware from getting on the machine by blocking suspicious malicious files (e.g.: Office docs), scripts, lateral movement, ransomware behavior, and email-based threats
- Network protection: Protects the endpoint against web-based threats by blocking any outbound process on the device to untrusted hosts/IP through Windows Defender SmartScreen
- Controlled folder access: Protects sensitive data from ransomware by blocking untrusted processes from accessing your protected folders
- Exploit protection: A set of vulnerability exploit mitigations (replacing EMET) that can be easily configured to protect your system and applications
To deploy a default set of Exploit Guard policy on Windows Server, you can run the following cmdlets:
[code language=”powershell”]
Set-MpPreference -EnableControlledFolderAccess Enabled
Set-MpPreference -EnableNetworkProtection Enabled
Add-MpPreference -AttackSurfaceReductionRules_Ids 75668C1F-73B5-4CF0-BB93-3ECF5CB7CC84 -AttackSurfaceReductionRules_Actions Enabled
Add-MpPreference -AttackSurfaceReductionRules_Ids 3B576869-A4EC-4529-8536-B80A7769E899 -AttackSurfaceReductionRules_Actions Enabled
Add-MpPreference -AttackSurfaceReductionRules_Ids D4F940AB-401B-4EfC-AADC-AD5F3C50688A -AttackSurfaceReductionRules_Actions Enabled
Add-MpPreference -AttackSurfaceReductionRules_Ids D3E037E1-3EB8-44C8-A917-57927947596D -AttackSurfaceReductionRules_Actions Enabled
Add-MpPreference -AttackSurfaceReductionRules_Ids 5BEB7EFE-FD9A-4556-801D-275E5FFC04CC -AttackSurfaceReductionRules_Actions Enabled
Add-MpPreference -AttackSurfaceReductionRules_Ids BE9BA2D9-53EA-4CDC-84E5-9B1EEEE46550 -AttackSurfaceReductionRules_Actions Enabled
Add-MpPreference -AttackSurfaceReductionRules_Ids 92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B -AttackSurfaceReductionRules_Actions Enabled
Add-MpPreference -AttackSurfaceReductionRules_Ids D1E49AAC-8F56-4280-B9BA-993A6D77406C -AttackSurfaceReductionRules_Actions Disabled
Add-MpPreference -AttackSurfaceReductionRules_Ids 01443614-cd74-433a-b99e-2ecdc07bfc25 -AttackSurfaceReductionRules_Actions Enabled
$url = ‘<a href="https://demo.wd.microsoft.com/Content/ProcessMitigation.xml">https://demo.wd.microsoft.com/Content/ProcessMitigation.xml</a>’
Invoke-WebRequest $url -OutFile ProcessMitigation.xml
Write-Host "Enabling Exploit Protection"
Set-ProcessMitigation -PolicyFilePath ProcessMitigation.xml
[/code]
Failover Cluster removing use of NTLM authentication
Windows Server Failover Clusters no longer use NTLM authentication by exclusively using Kerberos and certificate based authentication. There are no changes required by the user, or deployment tools, to take advantage of this security enhancement. It also allows failover clusters to be deployed in environments where NTLM has been disabled. Launch Windows Feedback for ServerClustering
Shielded virtual machines: Offline mode, Alternate HGS, VMConnect and Shielded Linux support
You can now run shielded virtual machines on Hyper-V hosts that suffer intermittent connectivity to their Host Guardian Service (HGS). Fallback HGS allows you to configure a second set of URLs for Hyper-V to try if it can’t reach the primary HGS server. Check out our blog to see how this can be used in a branch office scenario.
Offline mode takes the high availability promise for shielded VMs one step further and allows you to continue to start up a shielded VM even if the host’s primary and fallback HGSs can’t be reached as long as: 1) the VM has been successfully started at least once on that host and 2) the host’s security configuration has not changed since then. To enable Offline mode, simply run the following PowerShell cmdlet on the Host Guardian Service: Set-HgsKeyProtectionConfiguration –AllowKeyMaterialCaching.
We’ve also made it easier to troubleshoot your shielded virtual machines by enabling support for VMConnect Enhanced Session Mode and PowerShell Direct. These tools are particularly useful if you’ve lost network connectivity to your VM and need to update its configuration to restore access. VMConnect and PowerShell Direct will automatically become available for shielded VMs on a Hyper-V host running build 17040 or later.
Finally, for customers that run mixed-OS environments, we now support running Ubuntu, Red Hat Enterprise Linux, and SUSE Linux Enterprise Server inside shielded virtual machines. Try it out and send us your feedback in the Feedback Hub.
Encrypted Network in SDN
Network traffic going out from a VM host can be snooped on and/or manipulated by anyone with access to the physical fabric. While shielded VMs protect VM data from theft and manipulation, similar protection is required for network traffic to and from a VM. While the tenant can setup protection such as IPSEC, this is difficult due to configuration complexity and heterogeneous environments.
Encrypted Networks is a feature which provides simple to configure DTLS-based encryption using the Network Controller to manage the end-to-end encryption and protect data as it travels through the wires and network devices between the hosts It is configured by the Administrator on a per-subnet basis. This enables the VM to VM traffic within the VM subnet to be automatically encrypted as it leaves the host and prevents snooping and manipulation of traffic on the wire. This is done without requiring any configuration changes in the VMs themselves. Try it out and send us your feedback in the Feedback Hub.
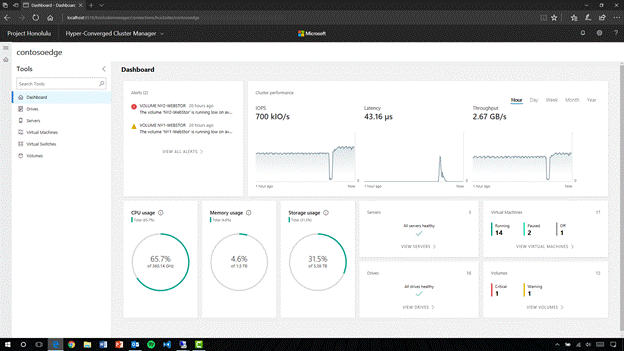
Performance history for Storage Spaces Direct
Administrators of Storage Spaces Direct can now get easy access to historical performance and capacity data from their cluster. Did CPU usage spike last night? When did this drive become slow? Which virtual machine used the most memory last month? Is network activity trending up or down? The cluster is pushing 1,000,000 IOPS – is that my new record?
Previously, you’d need external tooling to answer these questions. No more!
Beautiful new charts in Project Honolulu (and new PowerShell cmdlets, for those so inclined) empower you to answer these questions. There’s nothing to install, configure, or start – it’s built-in and always-on. Learn more at https://aka.ms/clusterperformancehistory.
Available Content
Windows Server 2019 LTSC Build 17623 is available in ISO format in 18 languages. This build and all future pre-release builds will require use of activation keys during setup. The following keys allow for unlimited activations:
| Datacenter Edition | 6XBNX-4JQGW-QX6QG-74P76-72V67 |
| Standard Edition | MFY9F-XBN2F-TYFMP-CCV49-RMYVH |
Windows Server vNext Semi-Annual Build 17623 The Server Core Edition is available in English only, in ISO or VHDX format. The images are pre-keyed – no need to enter a key during setup.
Symbols are available on the public symbol server – see Update on Microsoft’s Symbol Server blog post and Using the Microsoft Symbol Server. As before, matching Windows Server container images will be available via Docker Hub. For more information about Windows Server containers and Insider builds, click here.
This build will expire July 2nd, 2018.
How to Download
To obtain the Insider software downloads, registered Insiders may navigate directly to the Windows Server Insider Preview download page. If you have not yet registered as an Insider, see GETTING STARTED WITH SERVER on the Windows Insiders for Business portal
It’s all about your feedback!
The most important part of a frequent release cycle is to hear what’s working and what needs to be improved, so your feedback is extremely valued. Use your registered Windows 10 Insider device and use the Feedback Hub application. In the app, choose the Server category and then the appropriate subcategory for your feedback. Please indicate what build number you are providing feedback on. We also encourage you to visit the Windows Server Insiders space on the Microsoft Tech Communities forum to collaborate, share and learn from experts.
Known issues
- In‑place OS upgrade: Domain Controllers. During an in-place OS upgrade, Active Directory (AD) Domain Controllers (DC) might not be upgraded correctly. So, back up any AD DCs before performing an in-place OS upgrade.
- Editing or creating policies for AppLocker can cause the MMC snap-in to crash when generated rules for a packaged app.
- After upgrading the operating system, the AppX database may have corrupted entries, which causes problems for components that use those entries.
- Testing of the Windows core may fail because of a timeout while attempting to load the test libraries.
Terms of Use
All pre-release software made available to you via the Windows Server Insider program are governed by the Insider Terms of Use, which takes precedence over any license agreement that may be in the product.
No downtime for Hustle-As-A-Service,
Dona <3